Cisco Live 2025

Either by outright luck or doing something correct at work, my management deemed me worthy to get sent to Cisco Live in San Diego. This was actually my first business trip despite being with my currently employer for a number of years. I was excited to experience the Network Engineering Mecca as I’ve been told by colleagues past and present that it was essential to attend at least once in your career.
Cisco Live is formatted as a collection of curated classes, seminars, and labs over the course of a few days. Much of the content in all these categories is a hype-fest for Cisco products. But if you go into the conference with this perspective it won’t be as jarring and you can evaluate which events might be more worth your time rather than sitting through a useless sales pitch.
It was surprising to see how professional the conference was compared to the smaller, campy ones I had attended. There were many live commentary panels happening all over the conference building showcasing events for that day and had a seemingly national television quality equipment setup for all of them. Cisco even had a full audio and visual production staff at each of the sessions, which are recorded and available if you have a Cisco account.
Another part I wasn’t expecting was the provided breakfast and lunch each day. Considering the stereotypical perception of information technology workers eating junk food and being fat I went into the first meal not expecting much. But each meal was surprisingly healthy and delicious, which I hope is a reflection of the fading stereotype of IT workers being cranked on Mountain Dew an Doritos. The only time the food choices got lazy was on the last day of the conference, where breakfast was only cinnamon rolls and bananas. Not exactly ideal for someone watching their blood sugar. However, to Cisco’s credit, the last day of the conference was nearly a ghost town of attendance.
From the classes I attended I’ve included a shortlist of which ones I found rewarding to me personally. If there were slides for the presentation they are linked. Keep that in mind if the urge to photograph each of the slides hits you in a particularly interesting class. Access to a PDF copy of the slides is always better than a blurry image taken from the back row.
Classes
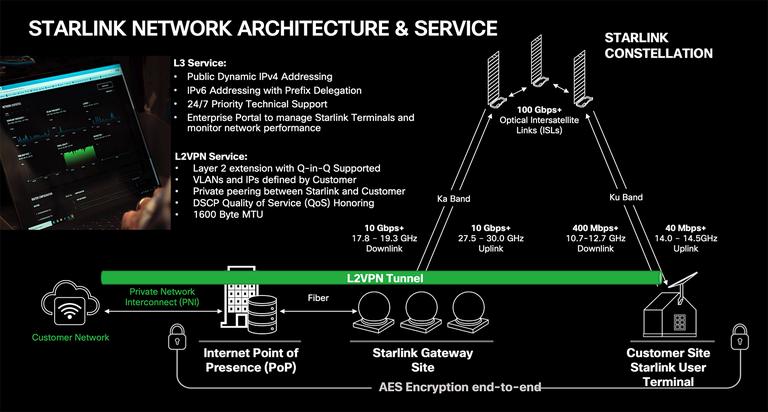
- BRKMSI-1000 Connecting the unconnected with Starlink & Cisco validated solution
- BRKOPS-1009 Dynamic Network Defense: Automating Traffic Engineering based on ThousandEyes Insights
- IBOSPG-2000 Let’s Talk Security: A Service Provider’s Perspective

- BRKMSI-2005 Internet Peering Design and Deployment
- BRKSPG-2080 Architectural Best Practices for Ensuring High Availability of IOS XR IP/MPLS Backbone Networks
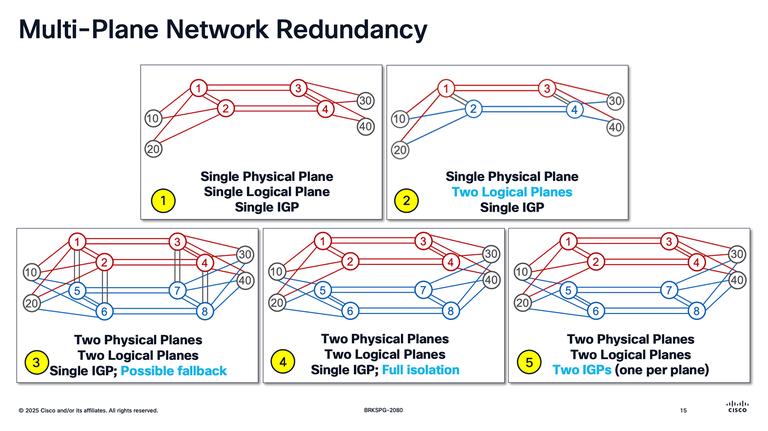
- BRKAPP-2021 Learnings Behind the Biggest Network Outages: Using ThousandEyes insights to improve IT resilience
- BRKENT-3219 Advanced Border Gateway Protocol

- CISCOU-1057 Packets in Space: Networking for the Final Frontier
- BRKMPL-2103 Mastering BGP: A Deep Dive into Basics and Design Best Practices for BGP and L3VPN

- BRKSEC-2499 Are You Prepared for the Next Typhoon?
- BRKMSI-1001 Secure the Network Edge against the DDoS Attacks!
There were certainly several themes that carried over among all of the classes. This was either through a collective effort by Cisco to urge and guide the industry or just separate teams identifying similarly important topics. The first was with authentication, both locally and through BGP peering. To illustrate the vulnerability during class, the instructor asked if someone could reveal the type 7 password on the screen. Within about 30 seconds someone had revealed the actual password with little more effort than a Google search and a simple web page utility.
username admin password 7 xxxxxxxxxxxxxx
The scary part is that this password type is still used in some environments. Perhaps through technical debt, being under staffed, or neglect, it leaves a stark vulnerability for a network compromise. Per the NSA, the recommended password type is currently 8, with 0, 4, and 7 marked as DO NOT USE.
Many classes expanded from this basic password hygiene to full system approaches like the Cisco IOS XR Software Hardening Guide. But the instructors didn’t spend much time besides highlighting that the guide was available to be used later on for engineers. One interesting perspective a few instructors shared is that the future approach by Cisco will be secure by default and only unsecured with configuration. So rather than ship a new router with telnet enabled, it will be disabled along with many other unsecure protocols or features. This methodology is in direct response to regulations coming out of the European Union and India, among others, to increase information technology security. By shipping secure, Cisco will defer the later unsecure configuration to the entities purchasing their products. Or another hope is to simply secure by attrition.

In the vein of better authentication tools, BGP TCP Authentication Option (AO) was frequently brought up as the new best thing for secure peering. Defined in RFC 5925, TCP AO adds a number of things that improve peering security over the older MD5 style. You can run a keychain with several keys that rotate over time. Meaning you could arguably update one of those keys without directly impacting BGP peering. Doing that with MD5 would cause a peer flap and can be disruptive. TCP AO also supports HMAC-SHA1 and AES-128-CMAC algorithms. Lastly, adding the TCP element to this allows for sequence tracking during the peering conversation, which can protect against replay attacks since you need to know the exact sequence to spoof a specific peer.


The exciting extension to the RPKI ROA architecture called Autonomous System Provider Authorization (ASPA), was mentioned in a few classes and I even got to try it out in my lab course. While still in the very early stages of public deployment and adoption, it addresses an easy vulnerability to a ROA. Although you can publicly declare to the world that you own a specific prefix with a published ROA, it doesn’t specifically restrict the BGP AS path to get to that prefix. Only the final AS in the path. A hijacker could theoretically announce your prefix with 1 extra AS in the path to attract traffic.

ASPA addresses this vulnerability by further defining the AS path and which providers are authorized to announce your prefixes. With it, you can define your service providers for the prefixes you own. It doesn’t cover the full AS path across the entire internet because the different paths are nearly infinite, however, it cements the important parts of the possible AS paths.
The concept of evaluating ASPA validity was conveyed to me in an interesting way through physical peaks and valleys. In this concept, the peaks are so called tier 1 service providers and the valleys are the so called access autonomous systems. In a valid ASPA path the valleys are limited to the beginning and end with the middle consisting of only service provider peaks.
After Hours
Only about half of the events happen during normal hours at Cisco Live. After classes and seminars are done for the day everyone migrates to the the restaurants and bars in downtown San Diego. It’s quite comical to see the flood of Cisco Live backpack wearing individuals spill out of the convention center and funnel to different locations. Step into any restaurant nearby and you’d see tables and tables of social networking in play.

While I’m a fan of computer networking and not necessarily social networking I still found the interactions rather fascinating. The interplay between vendors and clients on the ground was entertaining to say the least.


⁂